Sora Projects: easy configurations for every identity verification process
Sora’s central mission is to enable reusable identity across the internet. However, there are two key challenges to bringing that vision to life: every business has a different definition of user identity and businesses cannot rely on the identity verification decisions of others. That’s why we built Sora from the ground up with ultra-granular configurability in mind.
Today, we’re excited to announce Sora Projects, a powerful tool that allows financial services businesses to configure and optimize their identity verification processes for compliance, fraud detection, and user onboarding.
The challenge
Over the hundreds of interviews that we have conducted across fintech, crypto, and traditional financial institutions, we’ve found that the customization needs of each company vary drastically. For example, if you are a pre-launch fintech startup without a full-time compliance officer, you might be looking for a KYC solution out of the box and will look for a KYC provider to give guidance around the necessary checks for your use case. Alternatively, mature financial institutions might have fully-staffed compliance and fraud risk teams that are opinionated about specific use cases, jurisdictions, or product lines (e.g. an APAC-focused compliance team).
As we dug deeper, we discovered three major pain points our customers were facing:
- Existing solutions are not flexible enough to address each business’s unique fraud risk and compliance constraints
- Wrangling and optimizing data providers is time-consuming and requires significant expertise
- Legacy systems are too difficult to use
Given our observations, we sought to build a configuration product that empowers sophisticated risk and compliance teams while remaining easy to use for anyone.
Each business has unique needs
Different risk levels for fraud and compliance use cases
Consider a global payments company. For every payer, it has to perform Office of Foreign Assets Control (OFAC) and Politically Exposed Persons (PEP) screening. However, the transaction amount above a certain threshold triggers a requirement for government ID verification and a selfie match. This tiered approach encapsulates the principle of risk-based KYC screening—the higher the risk, the more stringent checks are needed.
In crypto, an exchange may face a different set of compliance requirements. For instance, the KYC needs for US users could differ significantly from non-US users. This exemplifies the geographical diversity of regulations, making compliance a more challenging task.
Jurisdictional nuances
Jurisdictional requirements for KYC can also vary dramatically. Each country or region has unique regulatory directives. For instance, Brazil mandates the verification of the Cadastro de Pessoas Físicas (CPF), a unique identifier for Brazilian citizens. Meanwhile, the UK mandates a well-defined verification requirement, adding another layer to the compliance process. The key here is understanding these regional specifics and implementing them without hampering the user experience.
It’s all in the details
Seemingly small nuances make a significant impact on businesses. For example, including elements like accommodating a second last name can reduce user friction significantly, especially in regions with a dominant Hispanic demographic.
Moreover, addressing the minutiae of compliance is essential. If a company cannot block an IP address location, address country, or government ID issuer to meet regulatory standards, the consequences can be severe. These factors underline the criticality of comprehensive and context-specific KYC processes, without which it might be a no-go from a compliance perspective.
To sum it up, the convergence of use cases, risk levels, and jurisdictional mandates creates a challenging compliance landscape. However, by investing in a nuanced understanding of these aspects, businesses can tailor a compliance approach that suits their unique needs while also creating a frictionless user experience. The goal should primarily be to strike the perfect balance between regulatory conformity and operational efficiency.
Why Sora Projects? A unique blend of flexibility and ease
Flexible and fully-featured
Sora achieves the level of functionality needed for a modern compliance team, without needing to cobble together legacy systems and burning excessive engineering resources. We are aware that the current marketplace’s proliferation of solutions raises the bar for configurability. However, the truth about orchestration functionality, flexibility, and user-friendliness varies considerably across the board.
We recognize that setting up a robust compliance infrastructure is the first and foremost step when launching a financial product. It’s crucial not only to get started quickly but also to ensure that the solution you choose is one that grows with your needs and doesn’t require a ‘graduation’ to a more comprehensive system down the line. Our solution is designed with this future-proof approach, making it a sustainable choice for growing businesses.
Streamlined onboarding and data optimization on autopilot
Sora Projects champions the cause of effortless onboarding and seamless iterations without the need for extensive coding.
Further, unlike pure orchestration layers, we’ve optimized our data provider stack and provide an opinionated system so you don’t need to worry about the tradeoff between data cost and quality. You may understand your end-users well, but it might not be your forte to delve into the nuanced differences between credit bureau and mobile carrier databases! That’s where we step in.
How it works
Identity verification (IDV) builder
Our identity verification builder is a dynamic tool that allows businesses to tailor their processes.
Each project offers an array of customization options:
- User Flows: Determine how verification steps are connected, decide which steps can be bypassed, and set the criteria for a manual review or outright denial.
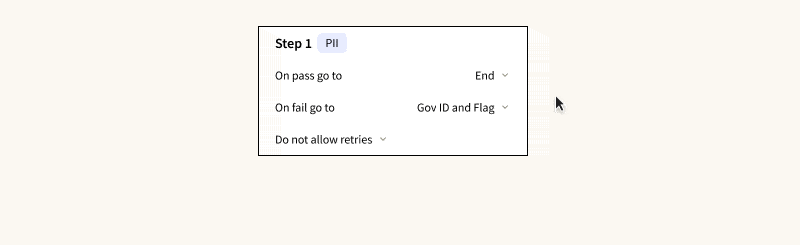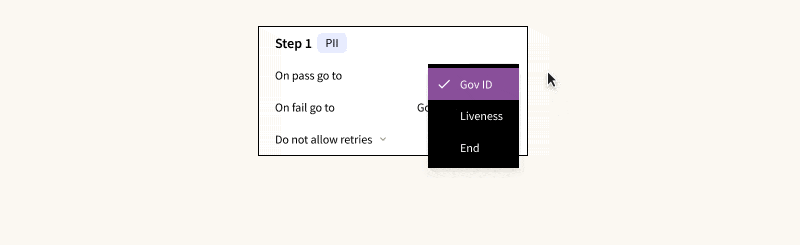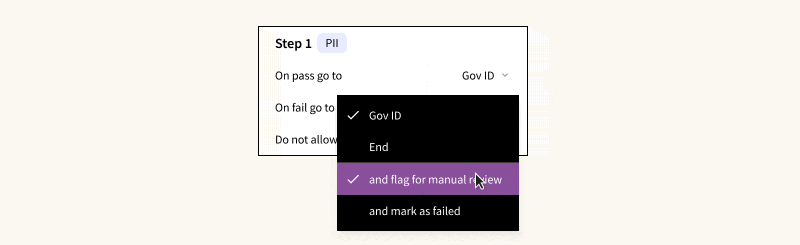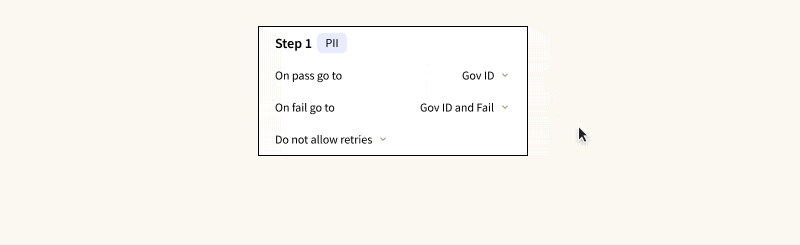
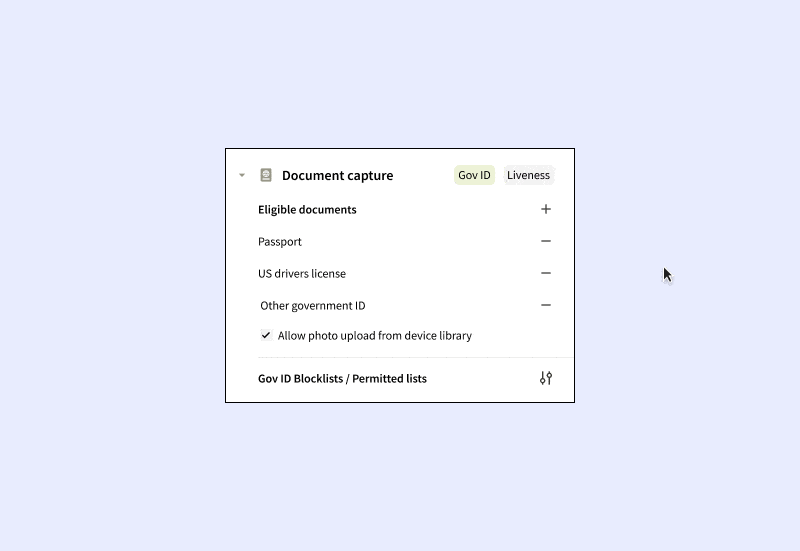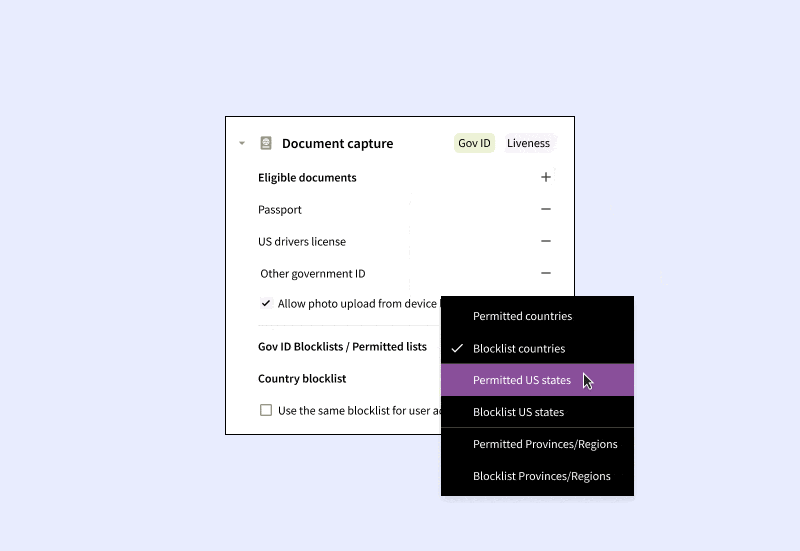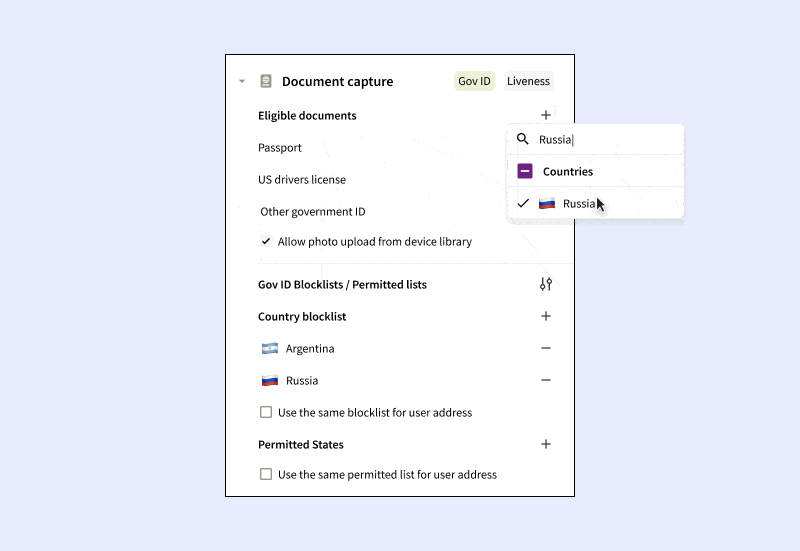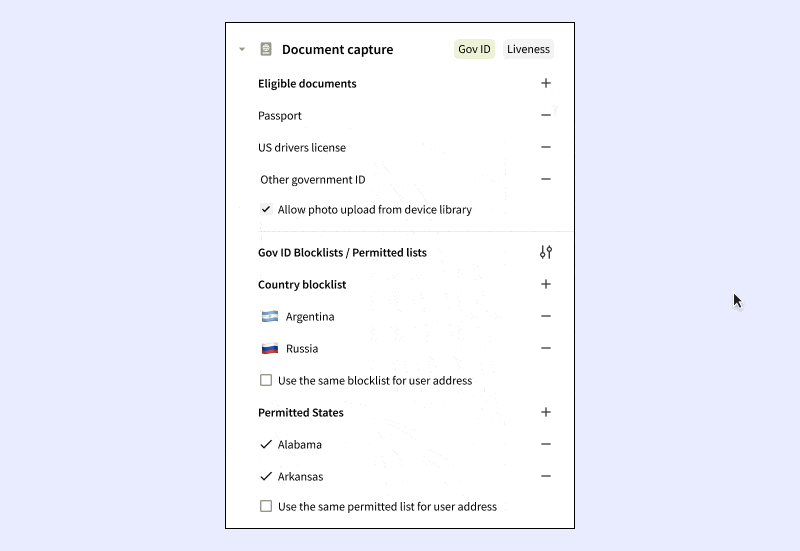
- Verification Steps: Define the specifics and logical sequence for each step such as address checks, Social Security Number (SSN) checks, government ID checks, device fraud checks, among others. Notably, you can opt to collect data from certain checks for future analysis without letting them affect the immediate verification outcome.
- The results are based on logical rules applied to individual checks, not just scores, which are accessible via API. This method simplifies any manual reviewer’s task of pinpointing the cause of a verification failure and remediating it accordingly.
- We provide a comprehensive range of verification types, including Basic Personally Identifiable Information (PII), SSN, Government ID, Selfie, OFAC/PEP/Adverse Media, Device Intelligence, Mobile Carrier Data Verification, Email Fraud Risk, and more. You can orchestrate the results of these checks effortlessly.
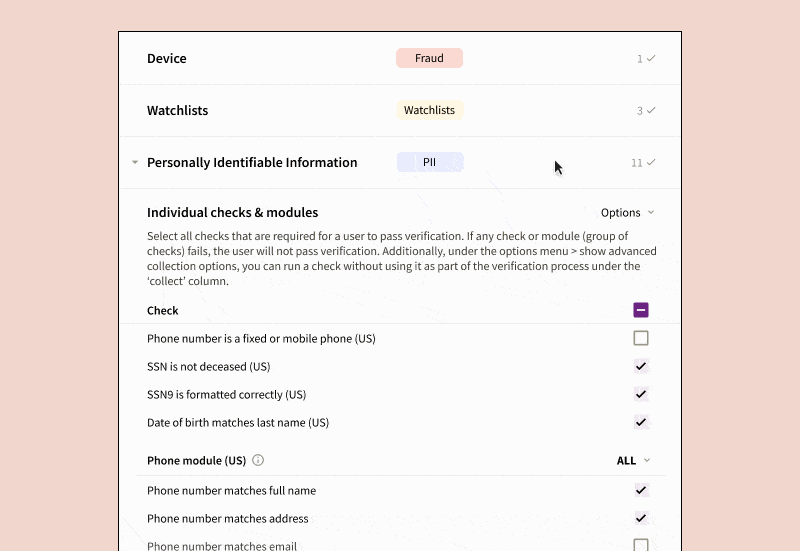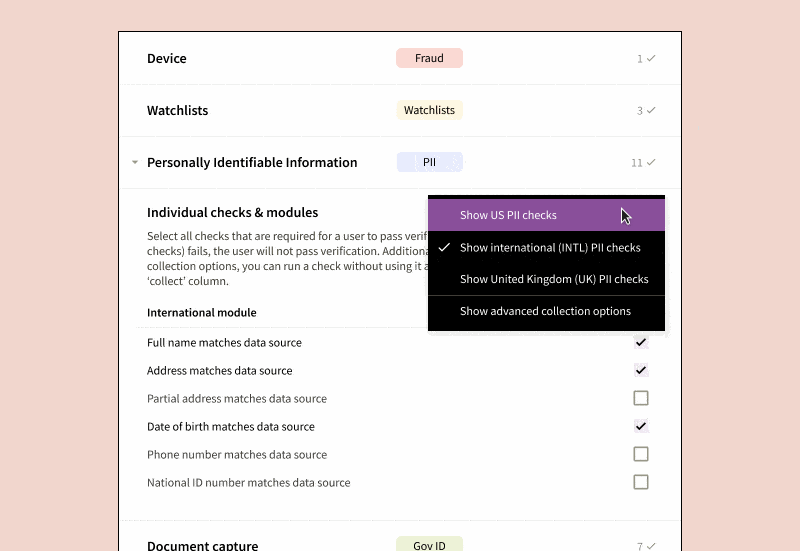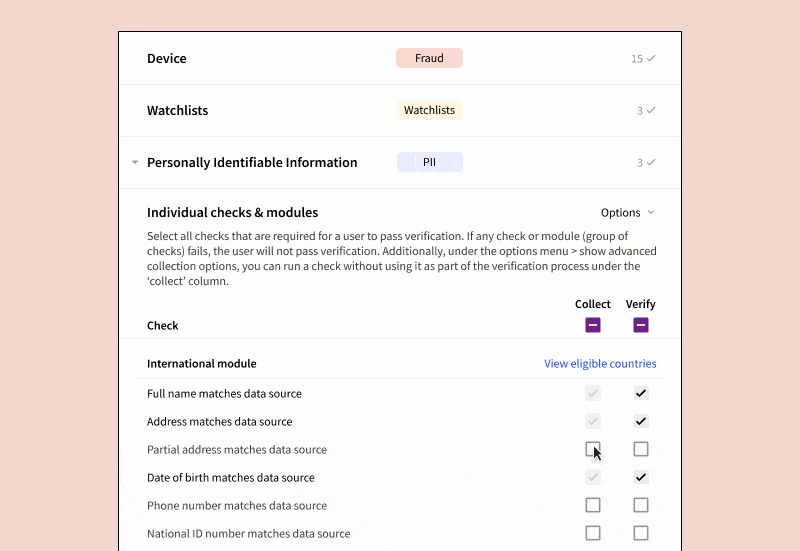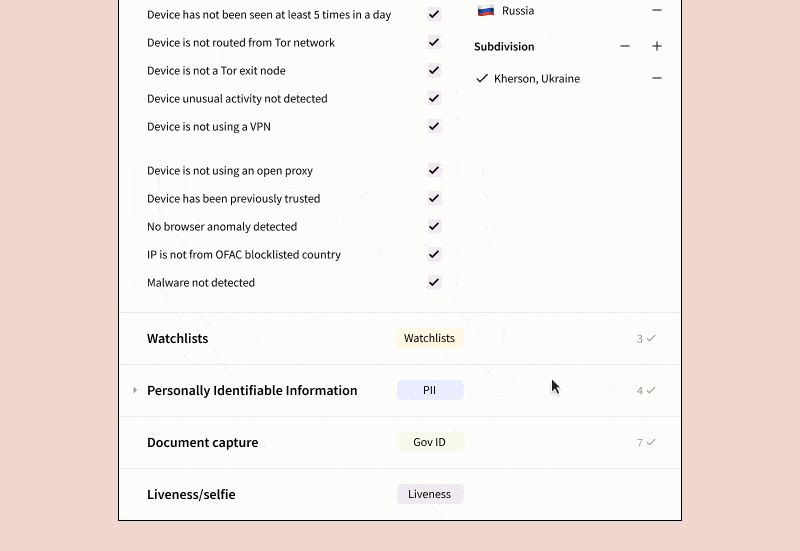
- Customer Traits: Set up specifications on the end-user traits to be collected. For example, you might choose to only gather passport data from certain countries, or establish blocklists for IP addresses, residential addresses, or government-issued IDs from particular regions or countries.
Personalized theming
Our white-labeled modal User Interface (UI) is customizable to align with your application’s aesthetics. You can edit elements such as the logo, text, link, and button colors to ensure a consistent look and feel with your existing application. When you are ready to go live, you can run through a verification session in “sandbox mode” before going live with your project.
Edit, test, and deploy multiple projects and versions
With our platform, you can craft multiple projects, each addressing different use cases, risk levels, and jurisdictional regulations. It facilitates a streamlined setup of your ID verification process but also supports subsequent editing, testing, and deployment. This approach ensures that your verification process remains as dynamic and adaptable as the business environment itself.
Interested?
Feel free to reach out at sales@soraid.com or schedule a time on our calendar here.
