- PRODUCT
Fast and secure identity verification
Sora links verified user identities to secure, portable cryptographic credentials. Each business that verifies the user can independently decision upon this data, eliminating redundancy without any reliance issues.
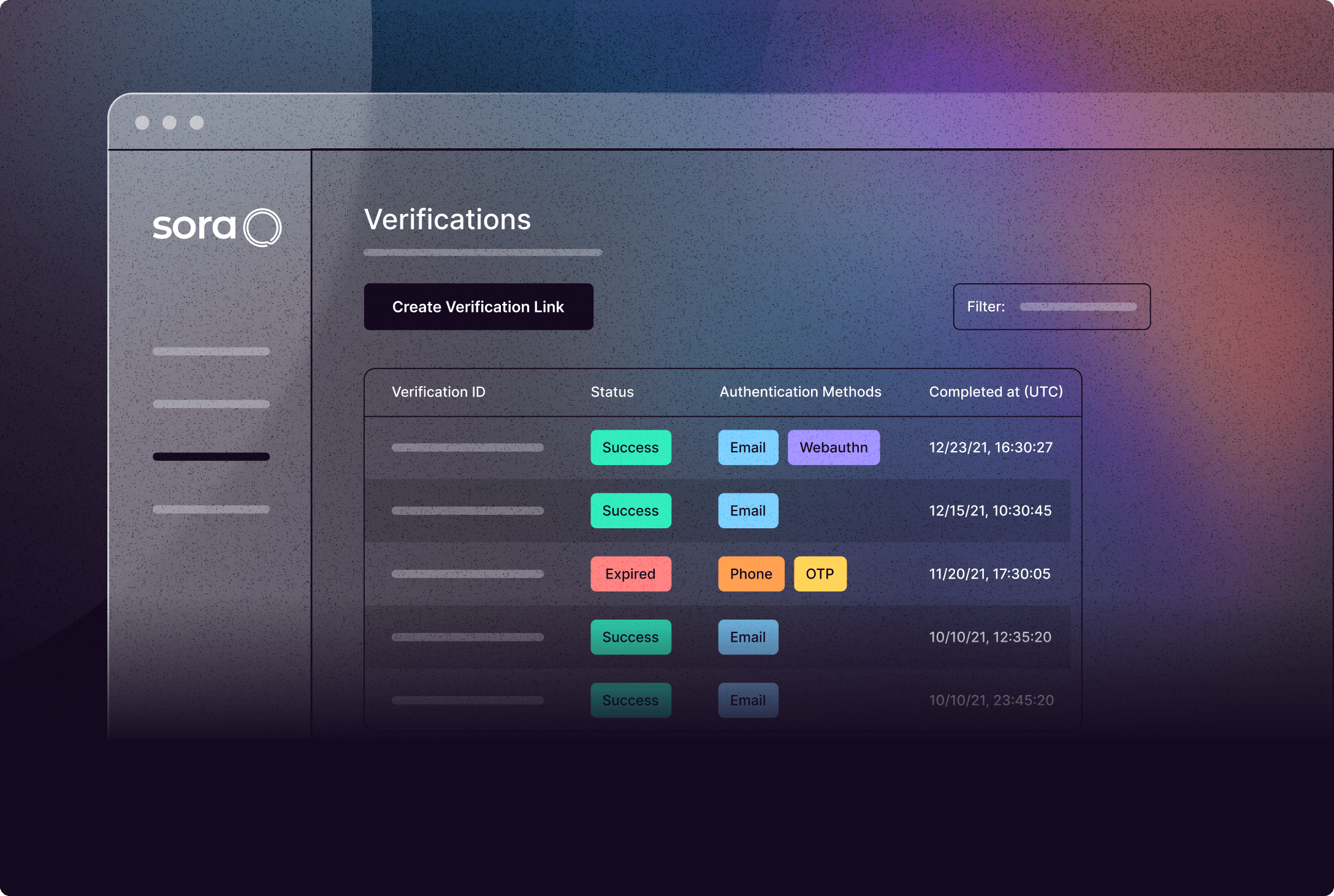
Identity verification reimagined.
Eliminate inefficiency in your identity verification process: improve passthrough rates, streamline user actions, lower costs, and reduce fraud.
Higher quality verification
Implement comprehensive verifications as each Sora ID credential becomes part of a network.
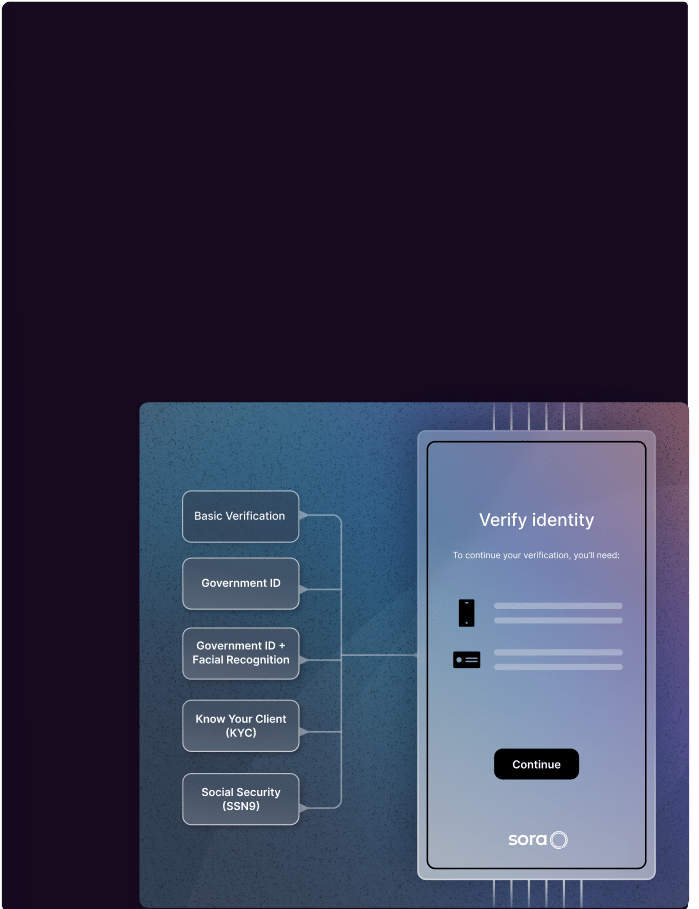

Best-in-class identity verification
When Sora verifies a user, we’re verifying them for our network, so our incentives are aligned with yours to verify more good users and reject more bad ones. We integrate with many data sources to optimize passthrough.

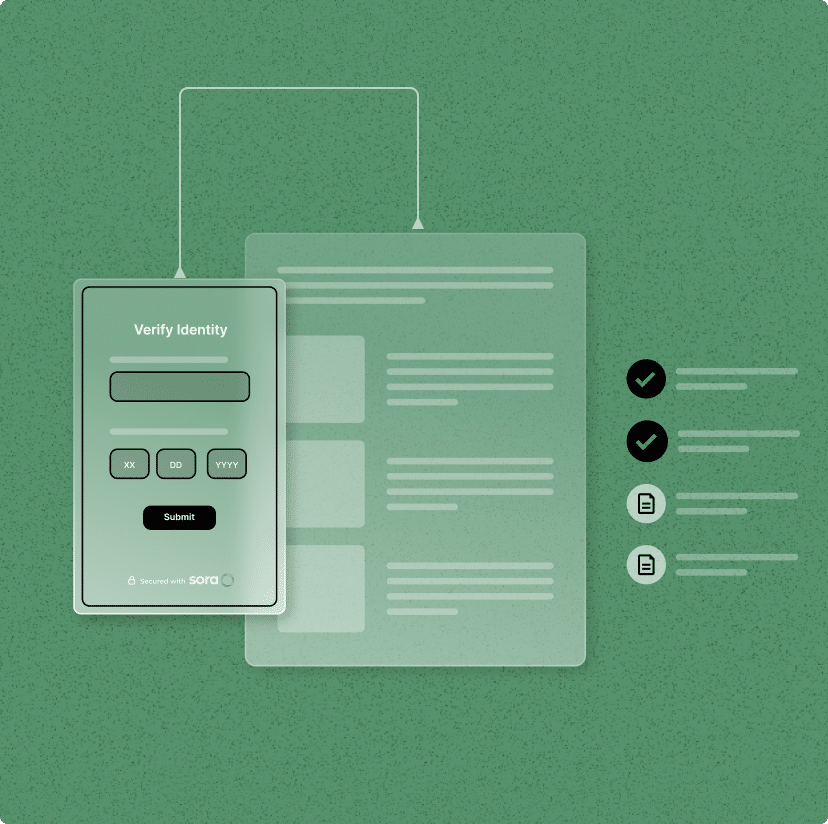
Easy customization
Configure your KYC decisioning flow and the look and feel of the Sora user flow easily through our dashboard, or use our optimized presets. See granular verification details and easily manage manual review if needed.

Eliminate the cost-quality tradeoff
Our network model allows us to offer high-quality IDV while also saving you money.

For developers, by developers
We take pride in making our API as simple and user-friendly as possible. If you have questions, you’ll be able to reach our technical team directly through a dedicated Slack channel.
Optimize IDV for your risk tolerance
Customize decisioning at a granular level to strike the right balance between conversion and risk. Leverage device and environmental signals along with multiple independent data sources to stop fraud before it happens.
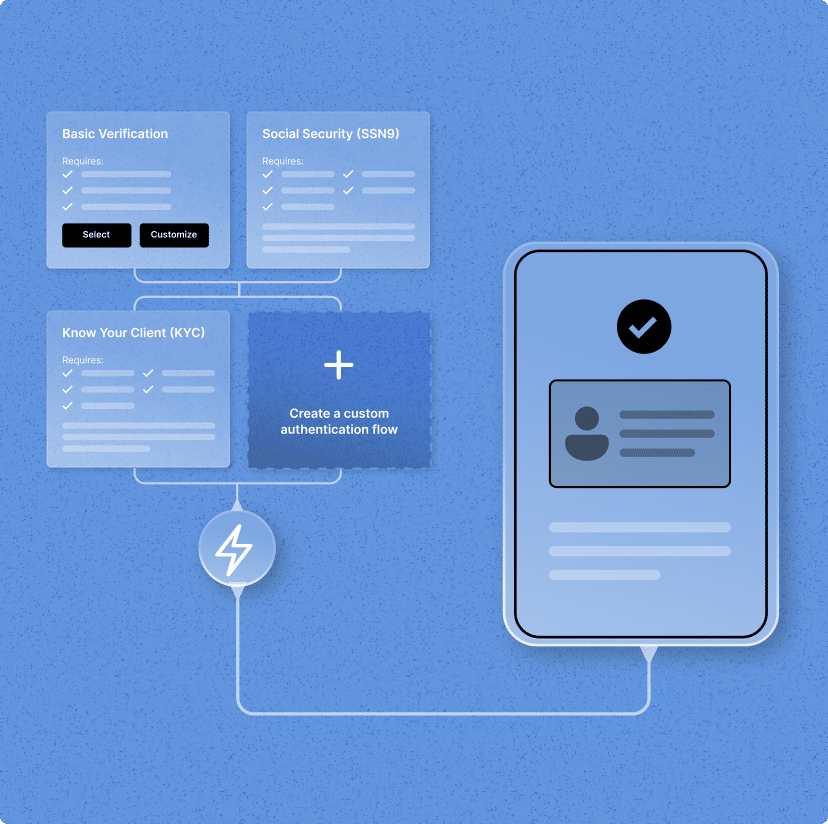
Flexible for every compliance need
Make decisions on common user data according to your own CIP—efficiency without reliance.
Easy front door, secure back door
The Sora ID doubles as a passwordless login credential. Decrease friction by authenticating your users with their Sora ID. Eliminate “forgot your password” attacks with biometric device-based login and secure account recovery.
How it works
We take privacy and security seriously



Customize your verifications to fit your risk & compliance needs
We check user information against many high-fidelity data sources with fallbacks so you can have confidence in all aspects of your user’s identity.